A recent report by McKinsey indicated that ‘spear phishing’ has increased seven-fold since the beginning of the COVID-19 pandemic.1 I’m sure that many of you have heard of phishing before but are unsure as to what spear phishing is and/or how it differs. Many people who are accustomed to identifying malicious phishing emails are still unfamiliar with what spear phishing is and could fall victim to a sophisticated attacker.
- Phishing
- In phishing attacks, bad actors cast a wide net of impersonal emails. They know that if they send to thousands of people, at least some of them are likely to fall for the scam and take the bait (e.g. clicking a malicious link, downloading malicious software, disclosing credentials via insecure websites).
- For example, an attacker may send an email impersonating Google to thousands of recipients informing them they need to reset their passwords with a link to do so. Upon clicking the link, recipients would then be redirected to a site appearing to be the Google password reset page, only to then handover their credentials to an attacker.
- Spear Phishing
- Spear phishing attacks are much more targeted, personal, and sophisticated than typical phishing emails, leveraging known information about an individual to manipulate them into providing sensitive data, transferring funds, or performing unauthorized actions.
- For example, an attacker may send an email impersonating the CEO of a company to individuals in financial roles requesting the transfer of funds.
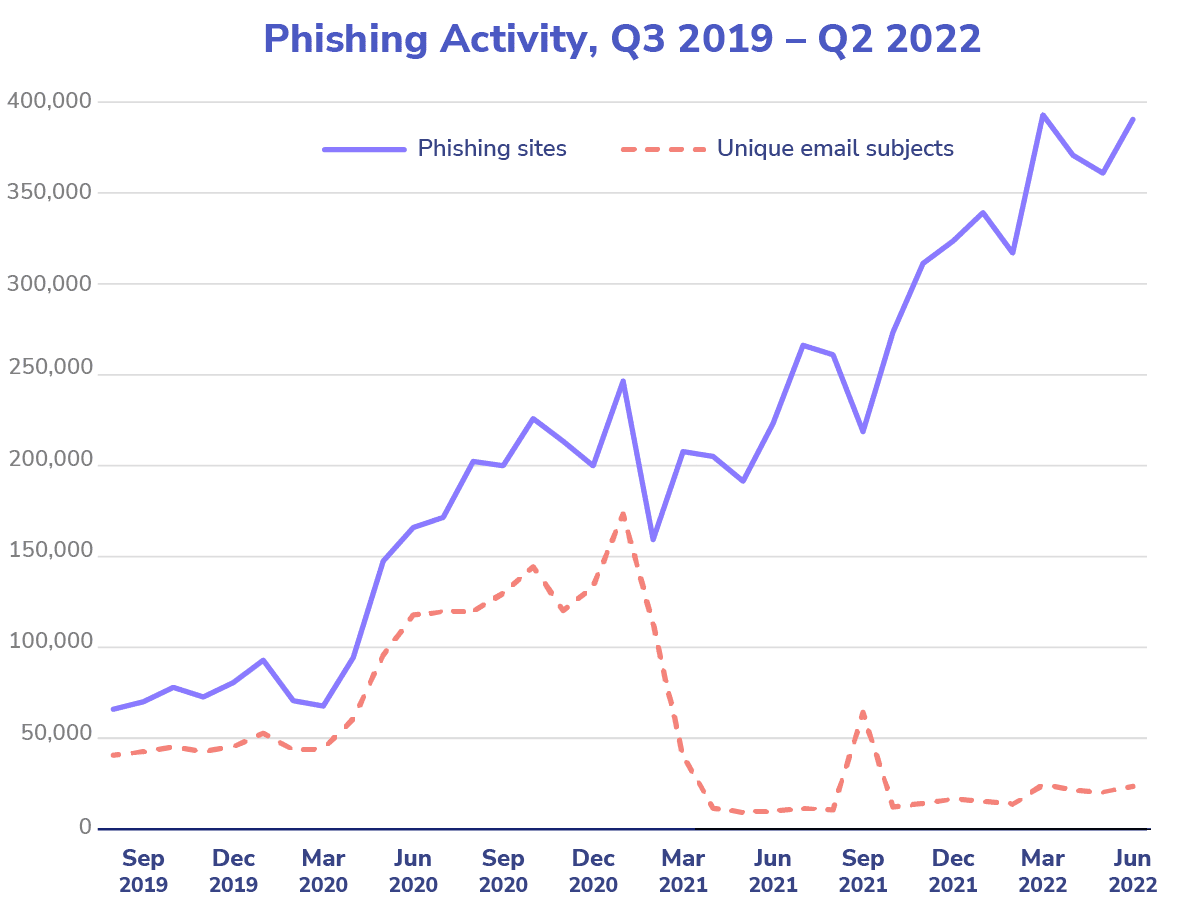
Source: APWG Phishing Activity Trends Reports, Q1 2020 – Q2 2022
The number of phishing attacks reported has quadrupled since early 2020. Yet, the number of unique subject lines used has dropped precipitously over the past couple years, as more emails have contained duplicative subject lines; this implies more accurate targeting of key accounts with subject lines proven to be effective in soliciting responses.
We’re continuously expanding our arsenal of technical and administrative safeguards
Consistent with the above data that shows spear phishing on the rise globally, we have also seen more and more spear phishing activity at Pearl over time. While it’s impossible to completely eliminate this type of risk, we’re continuously expanding our arsenal of technical and administrative safeguards to decrease the frequency of, and our vulnerability to, these types of attacks.
At Pearl, we’re committed to building technical and administrative safeguards into our systems to ensure that data from our company, our employees, and our customers is as secure as possible. As we develop our own data security best practices, we also believe in sharing this information with other organizations that may find it helpful.
To that end, below are some technical and administrative safeguards that you can put in place to make your organization less vulnerable to sophisticated spear phishing attacks:
1. Technical Safeguards
- Sender Policy Framework (SPF)
- SPF improves your email's reputation by allowing you to cache a list of authorized IP addresses that are allowed to send emails from your domain. SPF is a protocol that adds information to the message envelope. The downfall with this is that mail servers can remove sections of the envelope when a message is forwarded, eliminating this form of protection.
- DomainKeys Identified Mail (DKIM)
- DKIM allows senders to attach signatures to email headers and validate them using a public cryptographic key. It’s an email tagging system that does not filter or identify spam but prevent spammers from modifying message source addresses.
- Domain-based Message Authentication, Reporting & Conformance (DMARC)
- DMARC assists mail systems in deciding what to do with messages sent from your domain that fail SPF or DKIM checks.
2. Administrative Safeguards
- Security Awareness Training
- Security Awareness Training provides your staff with the knowledge needed to identify and report suspected phishing + spear phishing attacks.
- Phishing Campaigns
- Phishing Campaigns allow you to simulate attacks, and thus, put our staff’s knowledge to test and ensure you are consistently trending in the right direction.
We hope that you find the list of technical and administrative safeguards above informative and helpful so that you and your organization can put best practices in place to protect yourselves against spear phishing and other threats to your data security.
To learn more about data security at Pearl Health, read my blog on our path to HITRUST Certification, which explains why we’re building Security Compliance from the Ground Up.
- Venky Anant, Jeffrey Caso, and Andreas Schwarz, “COVID-19 crisis shifts cybersecurity priorities and budgets,” McKinsey & Company. July 21, 2020.